In recent months, we've seen the rootkit family Win32/Sirefef and Win64/Sirefef (also known as ZeroAccess Botnet)
update its command and control protocol and grow to infect more
computers while connecting to over one million computers globally
The ZeroAccess botnet not only
makes large amounts of money for its owners but it also causes
significant damage and loss in a variety of ways to a variety of
individuals and entities. Various aspects of ZeroAccess’ operation
consume considerable bandwidth. This is 1,227,300 bytes per hour,
29,455,200 per day and 895,929,000 bytes per month. 895 MB per month per
bot means a botnet with 1 million nodes could be producing as much as
895,000,000 MB or 895 Terabytes of network traffic per month. And all of
this occurs before any files are actually downloaded using the
protocol.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August
Before, disclosed that it creates its
own hidden partition on the hard drive and uses hidden alternative data
streams to hide and thrive. Then ZeroAccess developer changed infection
tactics and stopped using kernel-mode components in the latest version
Security firms tracked the growth of x64 version infections.
But Recently uncovered by SophosLabs that ZeroAccess botnet took a major shift in strategy and operating entirely in user-mode memory.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
They also disclose
the ZeroAccess has been installed on computers over nine million times
with the current number of active infected PCs numbering around one
million.
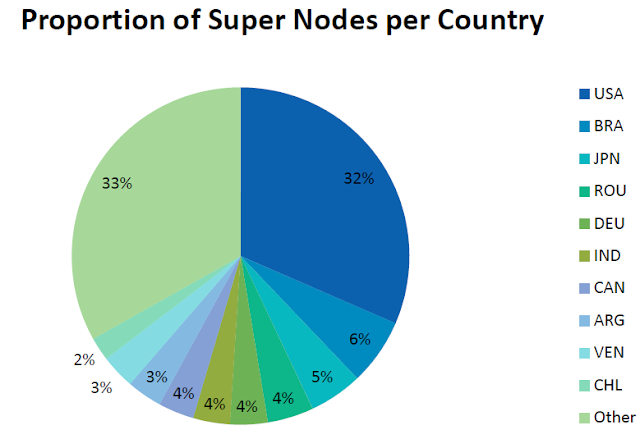
The current size of the botnet
is somewhere in the region of 9 million machines spread throughout the
world, but with the majority located in the U.S.
Other than U.S other top infected countries are :
- Brazil
- Japan
- Romania
- Argentina
- Venezuela
- Chile
The ZeroAccess botnet currently
creates two primary revenue streams: click fraud and Bitcoin mining.
Click fraud and Bitcoin mining can earn the botnet owners a potential
$100,000 a day. "The traffic generated by the ad-click fraud can burn
through your bandwidth cap. We have been following a number of bots
such as ZeroAccess whose primary function is ad-click fraud. These bots
receive instructions from a controller directing them to click on ads on
specific web sites. The web site owner gets paid by the advertiser on a
per click basis usually through the intermediary of an ad network. The
advertisers and ad network operator have a number of safeguards in place
to protect against click fraud," the report said.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August



No comments:
Post a Comment